Advanced Cybersecurity Assessment
IshanTech’s Penetration testing services provide comprehensive security evaluations through simulated cyberattacks to identify vulnerabilities before malicious actors can exploit them. Our certified ethical hackers conduct systematic penetration testing assessments across networks, web applications, and systems to uncover security weaknesses that automated tools might miss.
This essential cybersecurity penetration testing service helps Malaysian organizations strengthen their defense mechanisms against sophisticated cyber threats. We deliver detailed penetration assessment reports with prioritized remediation strategies to enhance your overall security posture and ensure compliance with industry standards.

What is Penetration Testing?
Penetration testing involves simulated cyberattacks by certified experts to assess the strength of your security defenses. Unlike vulnerability assessments that identify potential weaknesses, pen testing actively exploits discovered vulnerabilities to determine their real-world impact on your business operations.
Our penetration testing in cyber security methodology combines automated scanning with manual testing techniques, providing comprehensive coverage of your digital infrastructure. We conduct tests remotely via Internet connections or on-site for internal network assessments, ensuring thorough evaluation of your security landscape.
Penetration Testing Services –
Key Insights & Deliverables
Our penetration testing validates security controls through simulated attacks and real-world impact assessments, ensuring compliance with Malaysia’s Cyber Security Act while providing measurable risk metrics for informed security investment decisions.
We conduct comprehensive network penetration testing, web application security testing, mobile and desktop application penetration testing, system penetration testing for internal infrastructure, and social engineering testing to evaluate human factor vulnerabilities across your entire digital ecosystem.
Conduct penetration testing before launching new systems, following security incidents, during compliance audits, for merger and acquisition due diligence, and through regular quarterly or bi-annual security maintenance assessments.
We provide executive summary reports with business impact analysis, detailed technical reports with proof-of-concept exploits, risk assessment matrices with remediation timelines, step-by-step improvement roadmaps, and compliance gap analysis with regulatory mapping.
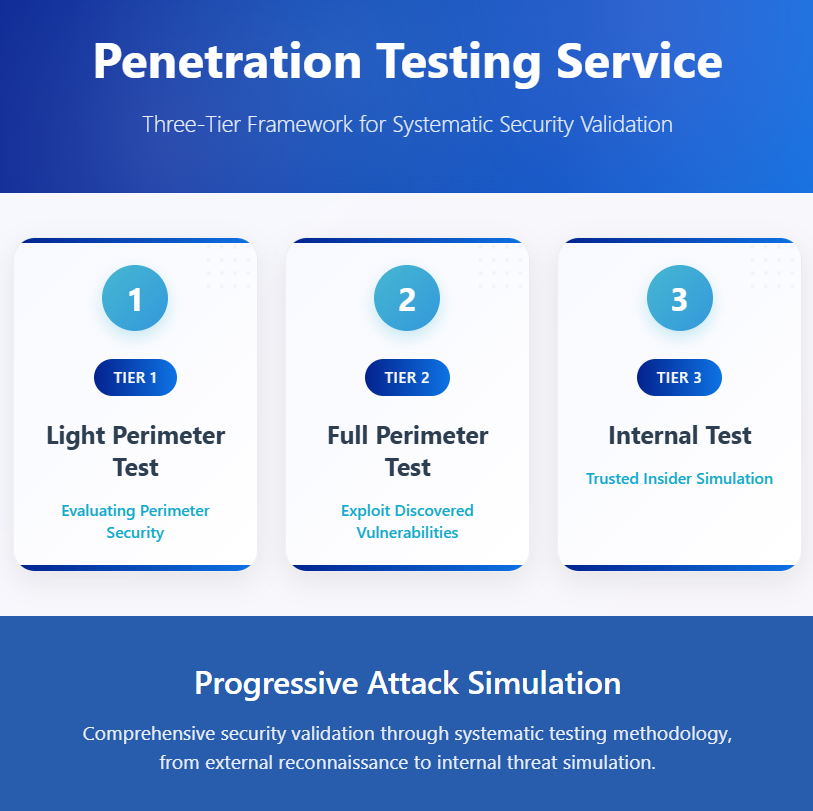
Audit Service Modes for Penetration Testing
Light Perimeter Test
Evaluating external perimeter security posture from a remote location outside your network’s boundary. This external assessment thoroughly evaluates your network’s outer defenses by realistically simulating attacks from internet-based threats, identifying vulnerabilities in firewalls, routers, and publicly accessible services.
Full Perimeter Test
A comprehensive verification of perimeter security, including remote exploitation attempts on DMZ servers and any accessible internal systems. This evaluation extends beyond basic perimeter scanning to actively exploit discovered vulnerabilities, testing server security and attempting controlled breaches of internal network segments.
Internal Test
The ‘trusted insider‘ test, where our consultants launch this test from inside the client’s network, with internal exploitation. This simulation replicates insider threats or compromised user scenarios, testing internal security controls, privilege escalation opportunities, and lateral movement capabilities within your trusted network environment.
Benefits of Our Penetration Testing
Proactive Threat Detection
Identify exploitable vulnerabilities before cybercriminals discover them
Enhanced Security Posture
Strengthen overall cybersecurity defenses through validated testing
Regulatory Compliance Assurance
Ensuring Adherence to Industry Standards and Malaysian Cybersecurity Regulations.
Cost-Effective Security Investment
Prioritize security spending based on actual risk exposure
Improved Incident Response
Quicker reactions to real-world cyberattacks, helping reduce impact and recovery time
Competitive Edge
Highlight your strong security posture to gain credibility with customers and partners.
Tools and Technologies Used in Penetration Testing
Our comprehensive cyber security testing approach leverages cutting-edge technologies and proven methodologies to deliver accurate, actionable security insights for organizations across Malaysia.
1. Testing Technologies
Advanced penetration testing frameworks and exploitation tools provide comprehensive coverage of IT infrastructure, web applications, and network environments with manual verification capabilities.
2. Assessment Methodologies
Structured cyber penetration testing approaches combining automated reconnaissance with manual exploitation techniques, employing industry-standard frameworks including OWASP, NIST, and PTES for consistent vulnerability identification.
3. Reporting Platforms
Professional systems generating executive-level summaries, technical findings, and actionable remediation roadmaps with risk scoring, visual dashboards, and proof-of-concept demonstrations.
4. Integration Capabilities
Seamless integration with existing security tools and IT management systems to streamline workflows and enhance overall security operations without disrupting business continuity.
5. Continuous Monitoring Solutions
Ongoing security assessment capabilities provide real-time visibility into your security posture with automated rescanning, threat intelligence integration, and proactive alerting systems.
Contact IshanTech today for comprehensive penetration testing services, customized to fit your organization’s security needs.