Comprehensive Security Evaluation
IshanTech’s Vulnerability Assessment involves a comprehensive evaluation of your digital infrastructure to identify security weaknesses before cybercriminals can exploit them. By systematically scanning networks, applications, and systems, our certified consultants detect programming flaws, configuration errors, and potential entry points that could lead to data breaches or system compromises.
This proactive cybersecurity service is essential for organizations in Malaysia seeking to strengthen their defence posture against evolving cyber threats. We provide detailed, actionable reports with prioritized recommendations to help businesses maintain continuous security and compliance with industry standards.
Vulnerability Assessment Services –
Key Insights & Deliverables
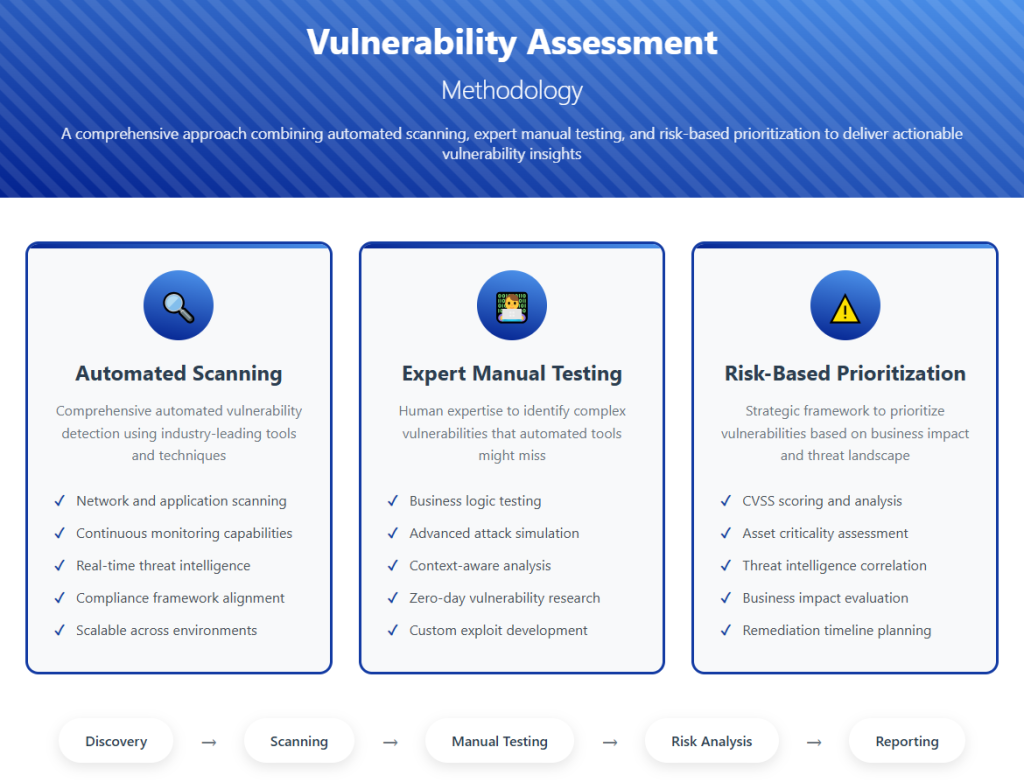
Detect security vulnerabilities in networks, applications, and systems before malicious actors can exploit them, while meeting regulatory requirements, including Malaysia’s latest Cyber Security Act and industry standards.
Comprehensive scanning of networks, applications, systems, databases, and cloud infrastructure, along with security review of mobile applications for both iOS and Android platforms.
- Before launching new applications, systems, or network infrastructure
- Following a security breach
- During compliance audit preparation
- Executive summary reports
- Technical vulnerability reports with remediation steps
- Risk assessment matrices
- Compliance gap analysis with improvement recommendations
Benefits of Our Vulnerability Assessment
- Reduced security breach risk
- Enhanced business continuity
- Recover data that may seem lost
- Cost-effective security investment
- Improved customer trust
- Competitive advantage
Tools and Technologies Used in Vulnerability Assessment
Our comprehensive approach leverages advanced technologies and proven methodologies to deliver accurate, actionable security insights for organizations across Malaysia.
1. Scanning Technologies
Advanced automated vulnerability scanners and network discovery tools provide comprehensive coverage of IT infrastructure, web applications, and cloud environments.
2. Assessment Methodologies
Structured testing approaches combine automated scanning with manual verification, employing industry-standard frameworks for consistent vulnerability identification.
3. Reporting Platforms
Professional systems generating executive-level summaries, technical findings, and actionable remediation roadmaps with risk scoring and visual dashboards.
4. Integration Capabilities
Seamless integration with security tools and IT management systems to streamline workflows and enhance overall security operations.
5. Continuous Monitoring Solutions
Ongoing vulnerability tracking and assessment capabilities provide real-time visibility into your security posture with automated rescanning, threat intelligence integration, and proactive alerting.
Contact IshanTech today for a comprehensive vulnerability assessment tailored to your organization’s needs.
Ready to strengthen your cybersecurity defences?
Overview of Purpose, Scope & Outcomes of Vulnerability Assessment
Purpose
Detect security vulnerabilities in networks, applications, and systems before malicious actors can exploit them, while meeting regulatory requirements, including Malaysia's latest Cyber Security Act and industry standards.
When to Perform
- Before launching new applications, systems, or network infrastructure
- Following a security breach
- During compliance audit preparation
Planning
Comprehensive scanning of networks, applications, systems, databases, and cloud infrastructure, along with security review of mobile applications for both iOS and Android platforms.
Deliverables
- Executive summary reports
- Technical vulnerability reports with remediation steps
- Risk assessment matrices
- Compliance gap analysis with improvement recommendations